letsencrypt作为一个公共且免费SSL的项目逐渐被广大用户传播和使用,是由Mozilla、Cisco、Akamai、IdenTrust、EFF等组织人员发起,主要的目的也是为了推进网站从HTTP向HTTPS过度的进程,目前已经有越来越多的商家加入和赞助支持。
Let's Encrypt免费SSL证书的出现,也会对传统提供付费SSL证书服务的商家有不小的打击。到目前为止,Let's Encrypt获得IdenTrust交叉签名,这就是说可以应用且支持包括FireFox、Chrome在内的主流浏览器的兼容和支持,虽然目前是公测阶段,但是也有不少的用户在自有网站项目中正式使用起来。
虽然目前Let's Encrypt免费SSL证书默认是90天有效期,但是我们也可以到期自动续约,不影响我们的尝试和使用。
官网建议使用certbot的acme客户端,以下也是用cerbort设置的,certbot官网有各个Linux发行版详细的安装教程,我使用的是rocky linux,和Redhat centos安装基本一致
一、安装snapd
certbot依赖于snapd,不安装的话无法运行
一般情况下使用
yum -y install snapd #安装snapd服务
来安装,然后
systemctl enable --now snapd #设置snapd开机自启
若要启用经典的 捕捉支持,需要设置链接,然后重启或者重新登录保证链接已生效
sudo ln -s /var/lib/snapd/snap /snap
如果已经安装,也可以使用
yum update snapd #更新snapd
然后将snap更新至最新版本
sudo snap install core sudo snap refresh core
二、安装certbot
如果之前安装过certbot,就需要先完全卸载之前的certbot
yum remove certbot -y
通过snap安装cerbort
sudo snap install --classic certbot
创建软连接,方便certbot命令的使用
sudo ln -s /snap/bin/certbot /usr/bin/certbot
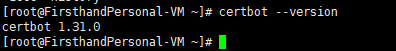
查看是否安装成功
certbot --version
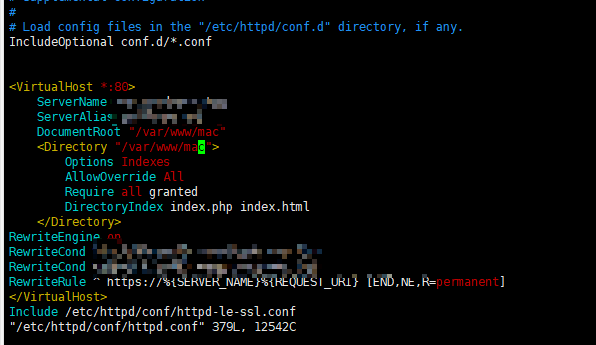
需要获取证书的站点在80端口,并且可以正常访问。监听80需要打开,如果是多站点,apache虚拟机也要监听80
certbot --apache #直接获取
certbot certonly --apache #获取证书,手动添加
使用certbot申请申请域名免费证书,默认会访问80端口,如果80端口不存在,会报以上错误,修改httpd.conf配置文件,添加上80端口,并重启apache
<VirtualHost *:80>
ServerAdmin test@test.example.com
ServerName www.test.com
ServerAlias test
DocumentRoot /var/www/html
</VirtualHost>
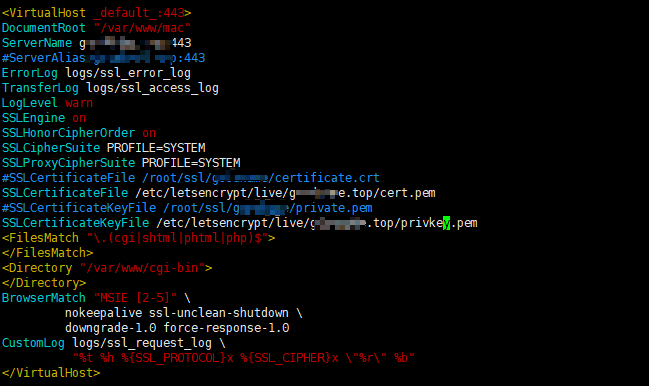
手动安装证书步骤
证书获取下来默认在/etc/letsencrypt/live/域名.top/目录,然后设置apache ssl.conf,设置完证书之后,重启apache,就可以了
测试自动更新
sudo certbot renew --dry-run
sudo certbot renew #更新证书
配置定时任务
30 4 * * 1 certbot renew --renew-hook "systemctl restart httpd" --quiet > /dev/null 2>&1 &
查看证书过期时间
certbot certificates
certbot certonly --nginx --email xxx@example.com -d a.do.com -d b.do.com #泛域名证书申请
certbot certonly -d *.example.com --manual --preferred-challenges dns --server https://acme-v02.api.letsencrypt.org/directory
certonly,表示安装模式,Certbot 有安装模式和验证模式两种类型的插件。
-d 为那些主机申请证书,如果是通配符,输入 *.example.com
--manual 表示手动安装插件,Certbot 有很多插件,不同的插件都可以申请证书,用户可以根据需要自行选择
--preferred-challenges dns,使用 DNS 方式校验域名所有权
--server,Let's Encrypt ACME v2 版本使用的服务器不同于 v1 版本,需要显示指定。
以下是自动生成的过程
[root@hostnamerocky8 player]# certbot
Saving debug log to /var/log/letsencrypt/letsencrypt.log
How would you like to authenticate and install certificates?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: Apache Web Server plugin (apache)
2: Nginx Web Server plugin (nginx)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2
Enter email address (used for urgent renewal and security notices)
(Enter 'c' to cancel): 545821208@qq.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.3-September-21-2022.pdf. You must
agree in order to register with the ACME server. Do you agree?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: y
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing, once your first certificate is successfully issued, to
share your email address with the Electronic Frontier Foundation, a founding
partner of the Let's Encrypt project and the non-profit organization that
develops Certbot? We'd like to send you email about our work encrypting the web,
EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: y
Account registered.
Which names would you like to activate HTTPS for?
We recommend selecting either all domains, or all domains in a VirtualHost/server block.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: goodvedio.top
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate numbers separated by commas and/or spaces, or leave input
blank to select all options shown (Enter 'c' to cancel): 1
Requesting a certificate for goodvedio.top
Successfully received certificate.
Certificate is saved at: /etc/letsencrypt/live/goodvedio.top/fullchain.pem
Key is saved at: /etc/letsencrypt/live/goodvedio.top/privkey.pem
This certificate expires on 2023-06-07.
These files will be updated when the certificate renews.
Certbot has set up a scheduled task to automatically renew this certificate in the background.
Deploying certificate
Successfully deployed certificate for goodvedio.top to /etc/nginx/nginx.conf
Congratulations! You have successfully enabled HTTPS on https://goodvedio.top
We were unable to subscribe you the EFF mailing list because your e-mail address appears to be invalid. You can try again later by visiting https://act.eff.org.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
If you like Certbot, please consider supporting our work by:
* Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
* Donating to EFF: https://eff.org/donate-le
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
[root@hostnamerocky8 player]#


发表评论